The Link Between Cyberattacks and Financial Crimes
Cyberattacks are often closely related to financial crime as the recent DOJ indictment charges show. We highlight key takeaways from the report.
Cylynx
February 26, 2021 · 5 min read
Cyberattacks are often closely related to financial crime as the recent DOJ indictment charges show. We highlight key takeaways from the report.
Cylynx
February 26, 2021 · 5 min read
Recently, the U.S. Justice Department charged three North Korean computer programmers who conspired to conduct a series of destructive cyberattacks to steal and extort more than $1.3 billion of money and cryptocurrency from financial institutions and companies.
The indictment report shows the interconnectedness between cyberattacks and financial crimes. Seemingly unrelated incidents are very much intertwined and connected. It also shows the scale and reach of state-funded criminal syndicates, with hacks and crimes across multiple industries and countries. Advanced persistent threats (APT), typically nation-states or state-sponsored groups have the resources and capabilities to breach critical systems.
In this article, we cover the threat of cybercrime to banks, the main key takeaways of the DOJ report and what financial institutions are doing to tackle such threats.
As per reports by Cybercrime Magazine, the total cost of cybercrime will reach $10.5 Trillion annually by 2025. And a significant portion of this will be directly linked with financial frauds.
Cybercrime, a computer-oriented crime concerns social media harassment, identity and data theft, phishing, hacking, etc. But in recent years, this crime has become synonymous with financial fraud. Banks have become the biggest victims of this due to the advent of digitization and automation of our financial systems.
Some of the most common types of cybercrime faced by banks and financial institutions include:

Phishing attacks or spear phishing typically relies on social engineering to gain access to a user's account. This could be targeted at a banking customer or more even employees of financial institutions. Accenture reports that three-quarters of banking companies they interviewed were targeted by such attacks.
Besides the threat of stealing customer funds, hackers also tend to leave malicious code which opens the doorway for further illegal activities such as ransomware attacks. Hackers could also use the compromised account as a backdoor to target critical systems such as internal banking databases or payment systems. Such incidents cost more than $118,000 to resolve.
The Carbanak attacks, an attack on an East European bank showed the speed and efficiency of hackers who used malware to conduct ATM cash-out thefts and alter database records to hide the trails of their fraudulent activities.

ATM Skimming is the use of a device planted on an ATM to gather data from any card that gets swiped. This device looks as if it is a part of the machine and goes unnoticed by consumers. Criminals often also place a small pinhole camera in a brochure holder near the ATM to extract the victims' pin numbers.
The data collected can subsequently be used to get access to victims' funds.

This is a broad class of fraud committed using credit or debit cards. where the criminals hack the credit card or credit account of civilians to make an unauthorized purchase. This could be application fraud where stolen credentials are used to open an account in the victims' name or even authorised fraud, where the genuine customer themselves process a payment to another account controlled by the fraudsters.
The U.S. Federal Trade Commission (FTC) reported that credit card fraud is the most common form of identity theft used by cybercriminals, accounting for close to 50% of all forms of identity theft.
With the rise of sophisticated fraud techniques, a compromised account's details may be held by a fraudster for months before any theft, making it difficult to identify the source of the compromise. Fraudsters often make small initial transactions to pass through conventional monitoring systems and to avoid raising an alarm.
Three men, namely Kim Il, Park Jin Hyok, and Jon Chang Hyok, residing in North Korea, are charged in the US for scheming to steal and extort more than $1.3bn from banks and other businesses.
These men were previously accused of being part of the Wannacry cyber-attack of 2017. Park Jin Hyok was also previously charged for his role in the 2014 hacking of Sony Entertainment Pictures.
The allegations contained in the DOJ report revealed how they conspired to compromise systems, steal data and money, and further the strategic and financial interests of the DPRK government and its leader, Kim Jong Un.
The three defendants are charged with the conspiracy to commit computer fraud and abuse, and the conspiracy to commit wire fraud and bank fraud. Yet, none of them is in custody as North Korea does not extradite its citizens to face US charges.
A Canadian-American man, Ghaleb Alaumary is accused of helping these men to launder the money. He has pleaded guilty to these charges and also admitted to being a money launderer for multiple criminal schemes, including ATM “cash-out” operations and a cyber-enabled bank heist orchestrated by North Korean hackers.
Quoting from, Michael R. D’Ambrosio, the U.S. Secret Service Assistant Director:
The individuals indicted today committed a truly unprecedented range of financial and cyber-crimes: from ransomware attacks and phishing campaigns to digital bank heists and sophisticated money-laundering operations.
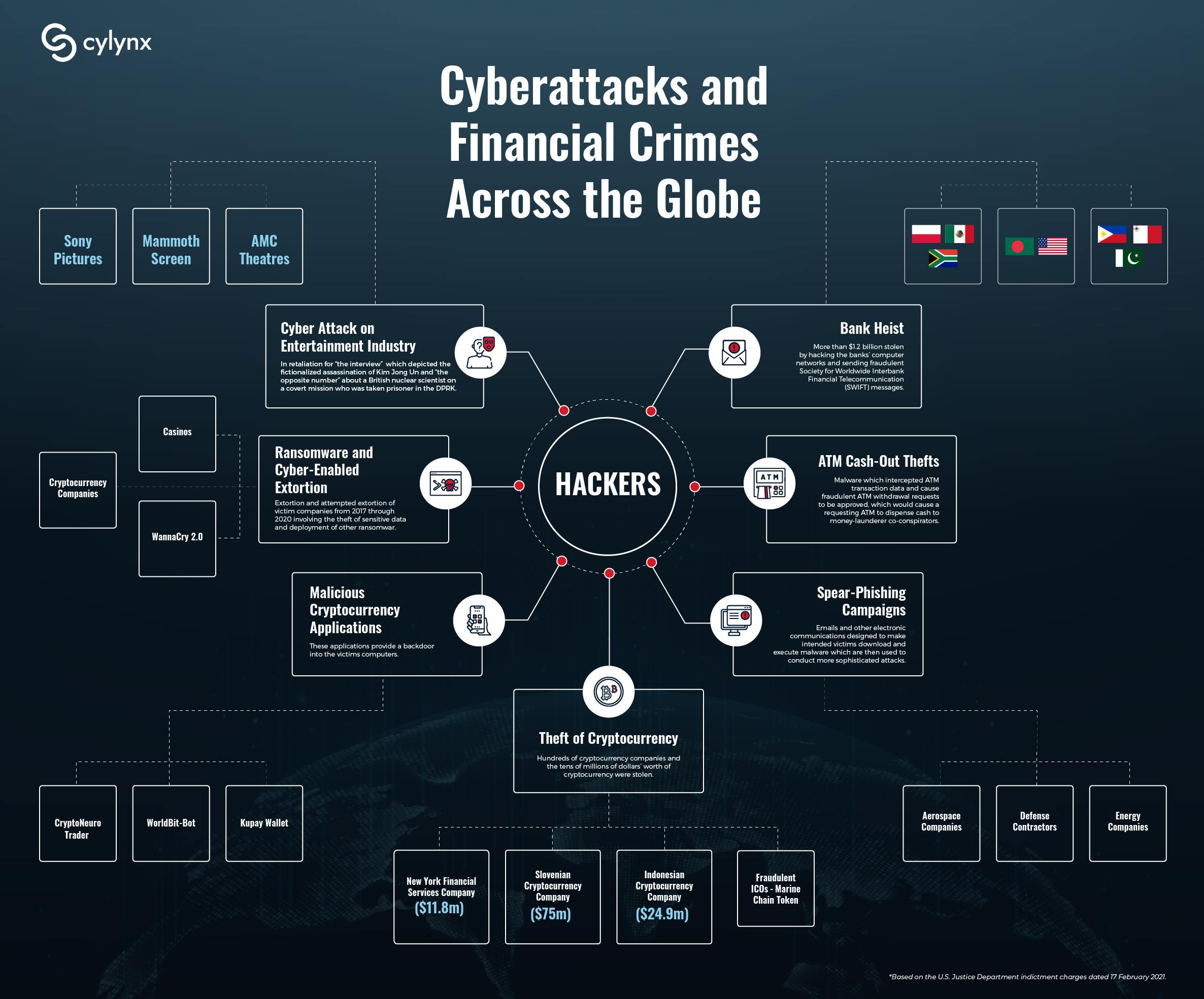
The infographic above shows the breadth and depth of cyberattacks and financial crimes conducted by the hackers. The full infographic is available for download at this link.
We summarise how the three defendants exploited cyber activities for revenge and financial gain:
An attack on the Sony Pictures Entertainment in December 2014 targeting AMC Theatres and an intrusion into Mammoth Screen, a production company producing a fictional series involving a British nuclear scientist taken prisoner in DPRK. These were conducted in retaliation for “The Interview,” a movie that depicted a fictional assassination of the DPRK’s leader.
A cyber-enabled bank heist from 2015-19 to steal more than $1.2 billion from banks in Vietnam, Bangladesh, Taiwan, Mexico, Malta, and Africa. The hackers attempted this by hacking the banks’ computer networks and sending fraudulent Society for Worldwide Interbank Financial Telecommunication (SWIFT) messages.
A cyber-enabled ATM cash-out theft also referred to as “FASTCash” by the U.S. government including the theft of $6.1 million from BankIslami Pakistan Limited (BankIslami) in October 2018.
WannaCry 2.0 ransomware attackin May 2017, and the extortion and attempted extortion of victim companies from 2017 through 2020.
Creating and deploying multiple malicious cryptocurrency applications from March 2018 through September 2020 to get a backdoor entry into the victims’ computers. These include applications such as Celas Trade Pro, WorldBit-Bot, iCryptoFx, Union Crypto Trader, Kupay Wallet, CoinGo Trade, Dorusio, CryptoNeuro Trader, and Ants2Whale.
Targeting and stealing tens of millions of dollars’ worth of cryptocurrency. This includes the development and marketing of Marine Chain Token to purchase fractional ownership interests in marine shipping vessels in 2017 and 2018. It was further supported by a blockchain, that would allow the DPRK to secretly obtain funds from investors, control interests in marine shipping vessels, and evade U.S. sanctions.
Spear-phishing campaigns in March 2016 through February 2020 targeting employees of U.S. cleared defense contractors, aerospace, technology, and energy companies, the U.S.Department of State, and the U.S. Department of Defense.
The indictment of the North Korean Hackers provides specific information to victims about how they had been targeted or compromised. The FBI and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, with the U.S. Department of Treasury, released a joint cybersecurity advisory and malware analysis reports (MARs) that highlights the danger of advanced persistent threat actors targeting individuals and organisations. It also identified the malware to belong to the “AppleJeus” family.
APT actors have targeted many organisations with the AppleJeus malware including the U.S, Singapore, U.K, Russia and China
Organisations should beef up their cybersecurity practices such as using updated software, installing a Host Based Intrusion Detection software and maintaining good network security practices.
Cryptocurrency users should exercise caution and verify the source of the links before downloading any application. Use of multi-factored authentication (MFA) for both user and device verification is recommended.
Financial institution and cryptocurrency companies should comply with top security recommendations such as the CCSS. Being the custodians of users money and with their trust and credibility on the line, financial institutions should take a holistic approach to risk management and examine the connections between seemingly minor security breaches and larger financial fraud.