Tracing a Scam Crypto Token (TMPL) Rug Pull
Blockchain forensics of the TMPL rug pull. We traced how scammers masked the trail of funds through mixer, gambling platforms, and cash out stolen ETH through exchanges.
Cylynx
May 27, 2021 · 4 min read
Blockchain forensics of the TMPL rug pull. We traced how scammers masked the trail of funds through mixer, gambling platforms, and cash out stolen ETH through exchanges.
Cylynx
May 27, 2021 · 4 min read
Previously, we wrote an article “The Rise of Cryptocurrency Exit Scams and Rug Pulls” mentioning what exit scams and rug pulls are, and the tracing of TMPL rug pull activities using Etherscan. A brief recap of what rug pulls are — they are a new form of exit scam whereby scammers posing as crypto developers abandon a project and run away with investors' funds by taking away buy support or Decentralised Exchange (DEX) liquidity pool from the market.
While the blockchain offers a scammer or hacker pseudo-anonymity, activities originating from suspicious wallets can still be traced. Leveraging our tracing algorithm, we traced the subsequent movement of funds from the TMPL rug pull that happened in 2020. In this article, we share more about how we traced the rug pull, our findings, and some sample outputs.
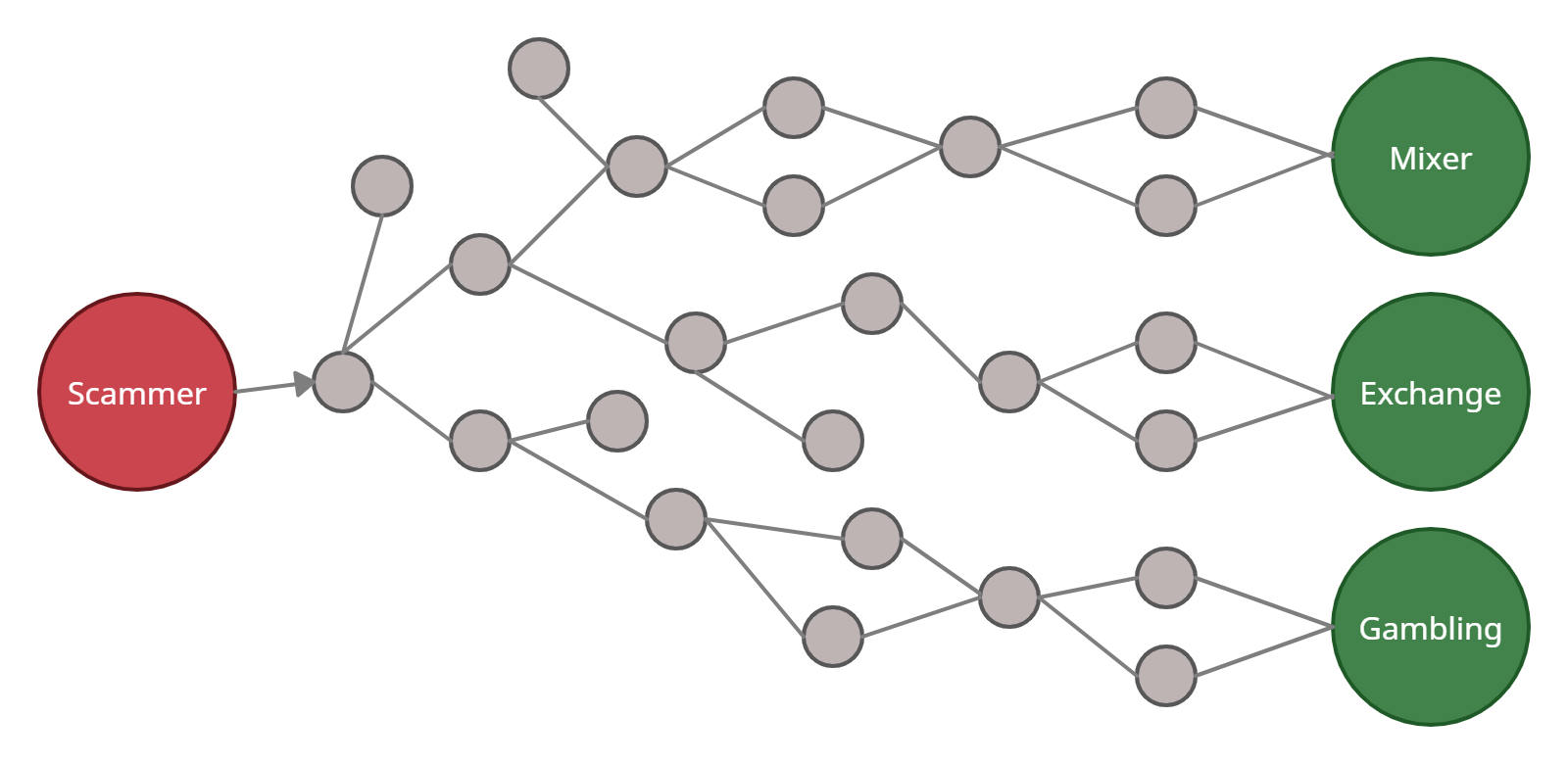
On August 15th 2020, TRUAMPL (TMPL) — a coin that mimics Ampleforth (AMPL) — was created and planned for a public sale on the Ethereum platform. It is an ERC20 token created on the Ethereum chain. Public sales are typically hyped up through marketing channels beforehand, in an attempt to attract potential investors to increase the worth of the token which aids in the development of the token.
As it turned out, the owner of the Ethereum contract address 0x5d64a2b59328c1e387806ebefaebcf57a45a298e maliciously pulled out the entire liquidity containing 154 ETH & 2,926,099 TMPL tokens. This was done just 40 minutes into the public sale of TMPL, after many traders exchanged their valuable ETH for TMPL token at the market rate as they feared missing out on the future price appreciation.
This resulted in the liquidity pool filling with more ETH tokens over time, enticing the scammer to pull the rug once his target has been reached. While all of the buyer’s TMPL tokens became virtually worthless after the rug, the scammer got away with about 154 ETH which was worth approximately 90,000 USD.
The TMPL exit scam analyzed in this report is one of a series of rug pulls that happened on the Uniswap decentralized exchange platform.
While the damage was already done to the investors, it is only the start for the scammer as he still needed to cash out the scammed / rugged funds. Typically, this involves moving the funds to centralized exchanges, OTC dealers or other fiat gateways and exchanging them for fiat. Let us take a look at our methodology to trace the trail.

Given an address, our tracing technology allows us to identify all funds that originated from any wallet of interest. This enables us to expedite the investigation process and automatically tag other suspicious wallets.
An automated approach to transaction monitoring allows us to keep track of all the wallets involved in the movement of hacked funds. For each transaction, we estimated the amount of ether associated with the main wallet by calculating the proportion of funds that could be traced back to its account.
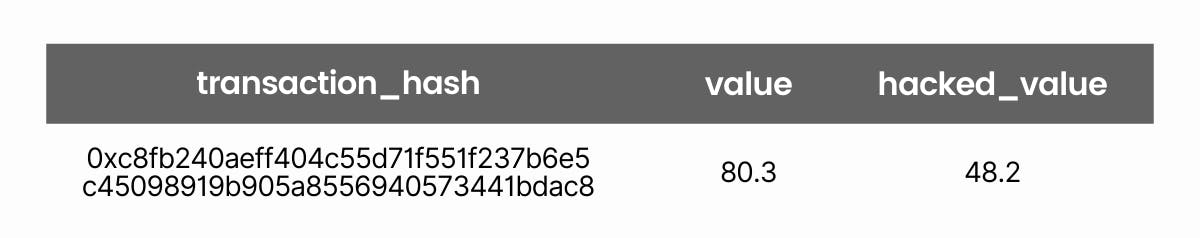
For an instance in the TMPL rug trail, our propagation methodology implies that for the above transaction, 48.2 out of 80.3 ETH transferred from the sender to the recipient is associated with the TMPL scammed funds.
Our monitoring technology highlighted above can help authorities and compliance officers find out the addresses that are related to the original scammer.
Subsequently, crypto exchanges can blacklist addresses to comply with regulatory demands or possibly freeze the accounts and return them to the right owners. One example, in which such action was taken is in the case of the Wine Swap exit scam where Binance recovered $345,000 worth of stolen funds.
The associated accounts can also be used to check if they contain any remaining funds. This can be collated as evidence for further law enforcement action or even seized by the authorities.
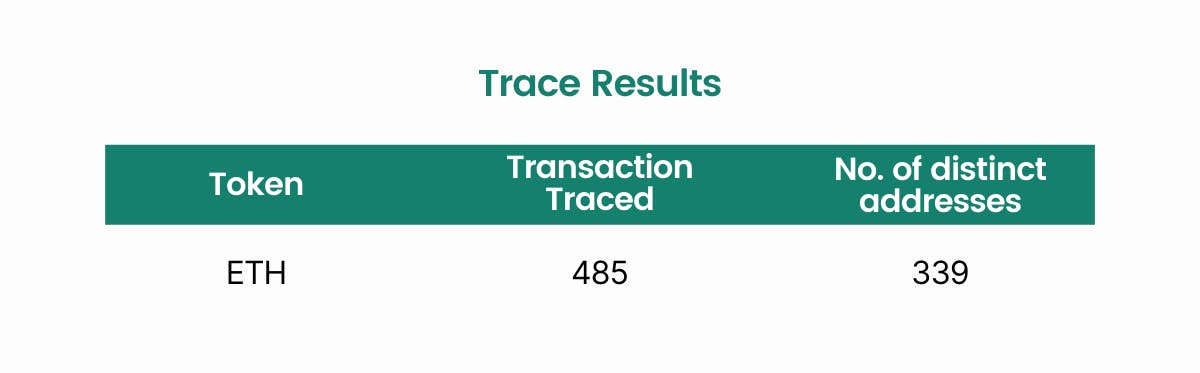 We have a total of 485 transactions and 339 distinct addresses that are associated with the transfer of the TMPL stolen funds from the above-mentioned contract address. Larger scale events such as the 2019 Upbit Hack can go up to more than 100,000 transactions and addresses, which our algorithm can handle.
We have a total of 485 transactions and 339 distinct addresses that are associated with the transfer of the TMPL stolen funds from the above-mentioned contract address. Larger scale events such as the 2019 Upbit Hack can go up to more than 100,000 transactions and addresses, which our algorithm can handle.
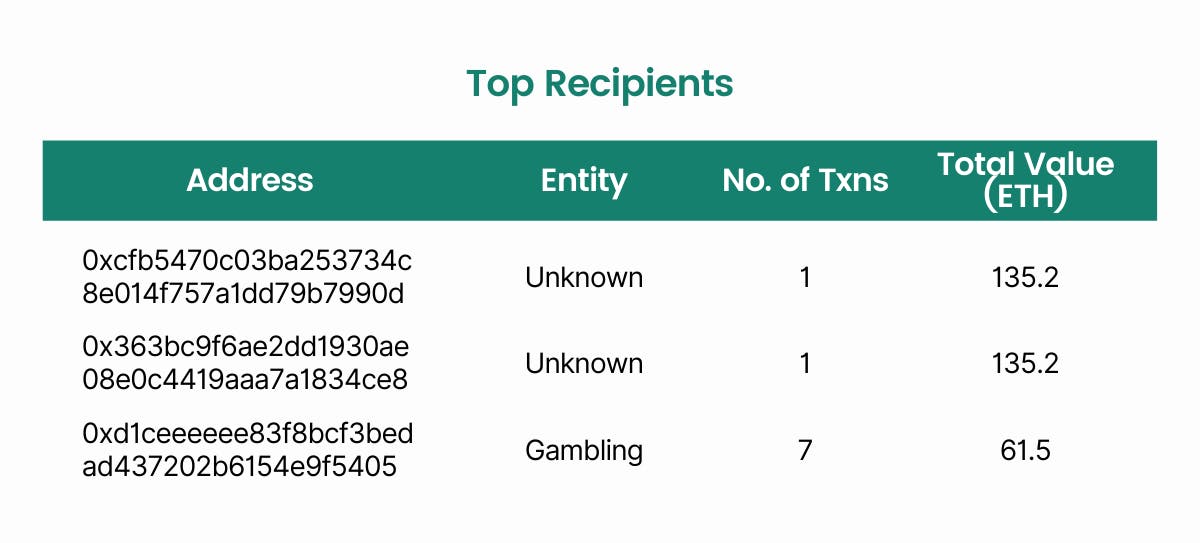
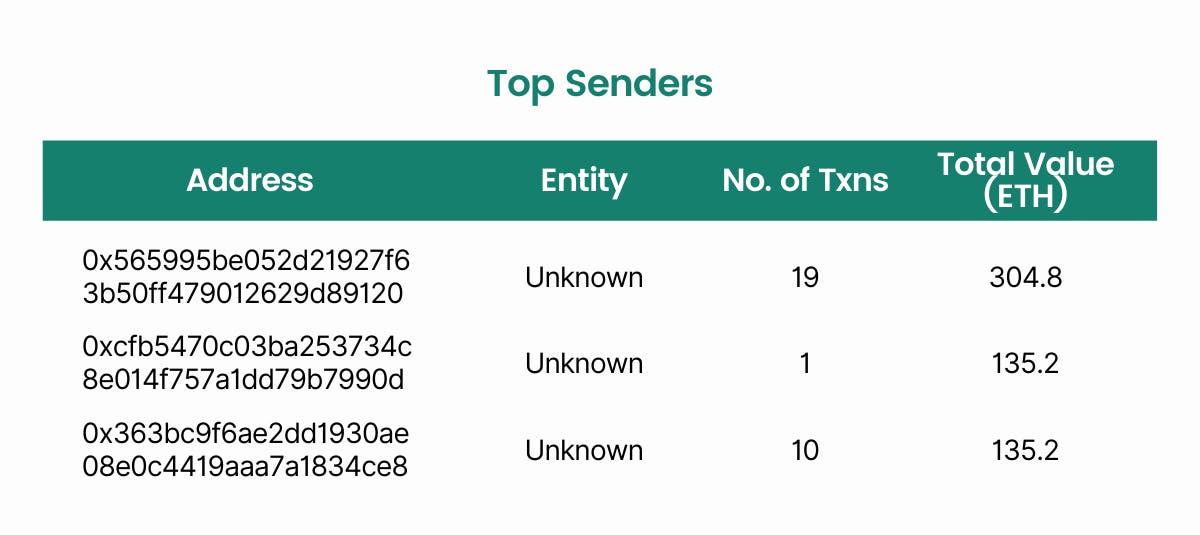
Next, we have a list of top senders and recipients in the trail by aggregated hack value or number of transactions. This is useful in identifying the key addresses that are influential in distributing the funds.
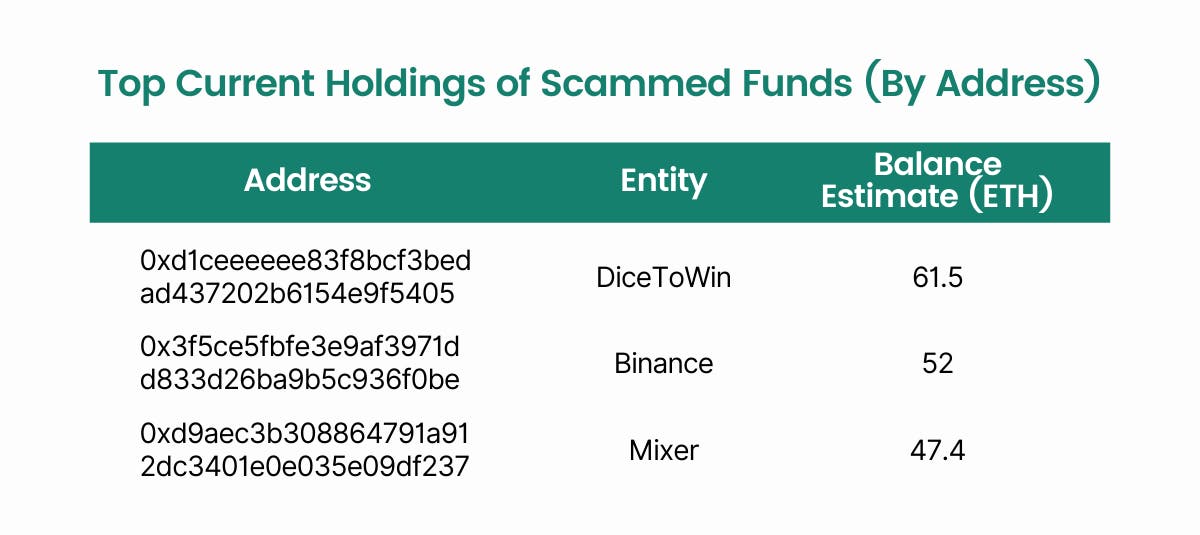
We can also track the current balance of rugged funds of the addresses involved. Most of the funds can be traced to entities such as mixers, exchanges and gambling sites. Mixer services and gambling platforms are commonly used by individuals to further obscure the sources of funds.
Once the trail has been masked, fraudsters often proceed to move the funds to crypto exchanges such as Binance and Coinbase to convert crypto into fiat. From our analysis, we find that about 27% of the TMPL rugged funds are still held in private addresses as of 21st May 2021.

This article highlights how we can trace the transactions, senders and receiver, and the current holdings of rugged funds. From our analysis, we highlight how scammers try to obscure the source of funds, eventually trying to cash out through exchanges.
While Know Your Customer (KYC) solutions are popular in the industry for regulatory compliance, they only provide a basic check at the point of application and should be supplemented by more robust tools.
Regulators and compliance teams should take full advantage of the transparency offered by the blockchain. A transaction monitoring platform such as what Cylynx offers aims to provide a more holistic risk assessment by aggregating information across all blockchain transactions. Get in touch with us here if you are interested in trying out our platform or want custom tracing of transaction trails.